Having done the Kioptrix series of vulnerable machines, I decided to head over to HackTheBox and attempt some of their beginner machines. I had heard good things about the HackTheBox platform in the past, and having now used it, I can’t stress enough how amazing of a resource it is.
After signing up, you are first presented with access to the HackTheBox network via OpenVPN. From here, you can remotely connect to any of their active boxes and attempt to achieve root access. I decided to pay for VIP membership for 1 month, as I wanted additional access to their ‘retired’ machines. These retired machines no longer need to be be kept secret, so have full walkthroughs available to them which provide an easier starting point for beginners. I can highly recommend the YouTube channel IppSec as learning material to go alongside these retired machines, as he extensively covers each one, often in more detail than simply attaining root.
HackTheBox is overall well constructed and very fun to use. with the added benefit of an active forum and progression system, HackTheBox provides assistance, motivation and a sense of community to enhance the learning experience. I would highly recommend at least looking into HackTheBox if you haven’t already.
With all that said, this week I owned 2 of the more simple retired machines, Mirai and Blue.
Mirai

As per usual, I started out with an Nmap scan to gather information on the services that were running on this machine. I found there was a web application running on port 80, but simply browsing to it did not seem to show anything.



To find out more about the web application, I ran the web application brute force tool DirBuster. Sure enough, I found there was an existing /admin/ directory and browsing to it presented a basic web application page. The interesting thing to note here is that it is running off a raspberry pi, which means it may be vulnerable to default credentials. A major hint here is actually in the title itself, as Mirai was the name of a malware which attacked raspberry pi IoT devices using default credentials to create a botnet in 2016.


Sure enough, I was able to make a SSH connection using the default credentials pi:raspberry and obtain the user flag. Easy!
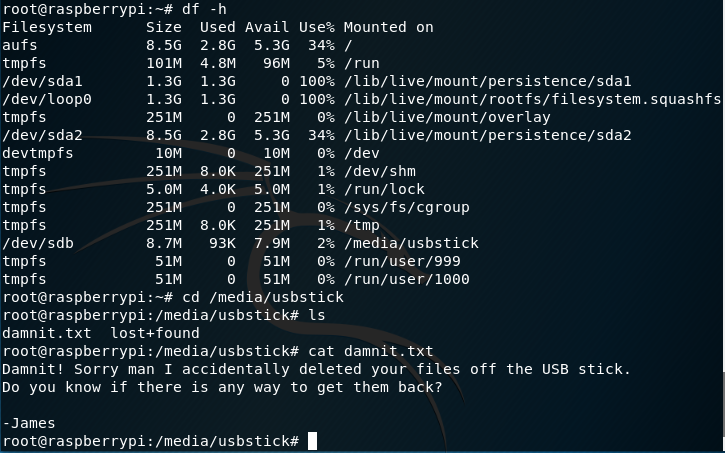
Browsing to root gave a message that the flag had been “deleted”, but may still be available on a USB stick. Browsing processes I could see a USB stick was plugged in, but browsing to that file again gave me another “error”. Damnit! (.txt)
I’ll admit that at this point I was stumped, and would not have been able to figure out how to find the previous contents of the damnit.txt file. Using IppSec’s guide, however, I was able to learn about the strings command and obtain the flag!
Blue
Another easy machine, Blue makes use of metasploit to exploit the EternalBlue vulnerability found in unpatched Windows 7 machines. Infamously, this vulnerability lead to the WannaCry Ransomware attacks which affected computer systems all over the world.

I started with the classic Nmap scan, but unfortunately this time I wasn’t able to find too much. I decided to try using some of Nmap’s scripting features to have a bit more of a poke around…


Running safe scripts on port 445, I found that the machine was “VULNERABLE“ to the ms17-010 exploit, otherwise known as EternalBlue. Like the previous machine, the hint for this one is found in the title itself.
From here, this machine was straightforward. I opened the metasploit framework, searched for the EternalBlue exploit and set the relevant parameters before exploiting the machine.



This gave me system level authority on the windows machine, and with that the two flags for this machine!
—
Both of these machines were fairly easy, Blue especially so. However I think there was a good opportunity presented in both to learn more about two high profile pieces of malware, and understand why and how they worked. The Mirai botnet and EternalBlue/WannaCry attacks were both very significant and had high exposure to the public. To learn more about these, their respective Wikipedia entries are a good place to start.
EternalBlue: https://en.wikipedia.org/wiki/EternalBlue
WannaCry: https://en.wikipedia.org/wiki/WannaCry_ransomware_attack
Mirai: https://en.wikipedia.org/wiki/Mirai_(malware)
—
I also want to give a quick shout out to a blog I recently discovered, VeteranSec. This is a blog with multiple contributors who write about various information security topics for beginners. I spent a good amount of time reading through their articles and found them to be helpful, motivating and encouraging.
In particular, I went over their two training topics; Practical Networking for Hackers and Linux Essentials for Hackers. Although I felt relatively comfortable with both of these already, I decided it would be worth dedicating time to revise them again. The Practical Networking for Hackers series in particular I found to be useful, and it remains an area I am still a little weak and inexperienced in.
That’s all from me this week, next week I plan to keep cracking on with HackTheBox, and start gearing up to starting the OSCP course.
Kento